DLP Strategy – Discover Strategies for Deployment Data Leakage Prevention
Talking about strategy of deployment data leakage prevention for business seems like daunting. It is so because this is not only about technology but, also about people and processes. This is obvious that groups in the firm might get affected by the unexpected loss of intellectual property or any other confidential data. Therefore, it is important to invest in a perfect Data Loss Prevention Technology because this can also be costly and time-consuming too. This blog will help users by providing ideas, to begin with, slow for an effective DLP strategy.
Best Exercises To Implement DLP Strategy Successfully
Before jumping directly to the DLP strategy, users are suggested to learn some best practices. These are to be adopted for successful pre and post preparation of the data loss prevention service.
- Deeply learn that what is the need of DLP in your business.
- Identify the confidential and secretive data that might harm your business.
- Check whether the chosen DLP service or software supports all data formats, which are used in your organization.
- Implementation of DLP should begin from minimal point for handling false positives. This point should be upgraded with more identifications of crucial data.
- The data loss prevention activities should be well-enough to arrange false positives and the fine tuning separately from DLP policies.
- A RACI matrix needs to be setup for drawing out all the responsibilities of DLP implementation, policies, etc.
- A proper documentation needs to be updated including the risk profiles and DLP incidents.
Terminology of DLP Strategy
The data loss prevention software comes with built-in policies, which are already following compliance standards like HIPPA, SOX, PCI, etc. Firms just have to utilize the policies with respective organizational footprints. Well, the core thing in DLP strategy is to decide files and folders, which needs to be protected at any cost. This is required to reduce the overall false calls on large number of data. The following points will help users in exercising the data classification:
1. Identify the Sensitive Data: This is most crucial stage where organization needs to determine that what information is important to them. It is so because this factor could affect the organization growth and hence, also vanish firm if the data is in wrong hand. Data loss prevention services work with capability of identifying bounded items when someone is trying to cross its boundaries. For identifying crucial items and developing their signature, there is a word in DLP software named as fingerprinting. This kind of valuable information is saved in several formats at any location in the firm, which requires identification and fingerprints.
2. Defining the DLP Policies: When organization is done with discovering of confidential data, they need to create data loss prevention policies for data protection. Each policy must be having some set of rules like PII, social security numbers, and credit card numbers. One can use regular expressions to create new rules if existing rules are not supporting data out of the box.
Point to Remember: At this stage, person should only define DLP policies but, not apply them.
3. Finding Information Flow: The DLP strategy states that organization needs to identify their business data flow. A set of questions should be prepared in mind to determine and retrieve essential information related to Data Loss Prevention Implementation. Following are few sample questions:
- What are all procedures they’re in place of growing the informational flow?
- What must be the initial and end point of the identified information?
- What are all issues present in the public or private network?
4. Determine the Owner’s Data: At the time of planning, identification of the business owner’s data is very much important. Prepare a sheet on which you have to describe all files, which are sensitive and secretive for the owner.
5. All Possible Planning Scenarios: The confidential data can be classified into 3 parts: data at rest, data in motion, and data in use. Once users are done with identification of sensitive data and policy defined, now they have to setup a plan for DLP product. The following points cover DLP planning scenarios for all these three types:
- Data in Motion: This involves data protection when files are transmitting through cables, wires, etc. This comprises of channels like SMTP, IM, HTTP/S, FTP, etc.
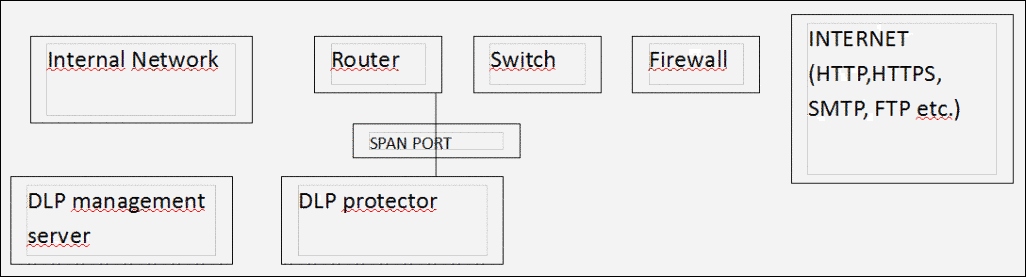
- Data in Use: The information needs to be saved that is stored at the end user workstation. Basically, it is to be safe from data being getting leaked by portable storage devices. In this type of scenario, the agent is already installed at every point of the device like PC, which is filled with the policies. Not only this but, agent is also capable of managing data by the centralized DLP management server. These agents could be spread on endpoints through the pushing strategies like GPO, SMS, etc. Apart from all this, the communication port must be appended as the exception in list of the local firewall.
- Data At Rest: The files, which are archived on the server and database have to be monitored regularly from being getting leaked. This type of data is stored on the storage server or component, which are crawled with DLP crawling agent. When crawling gets finished, information is fingerprinted for seeing unstructured data that might be present or might be not.
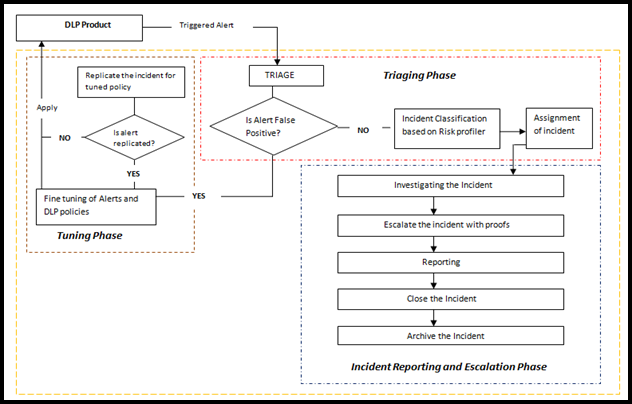
6. Data Loss Prevention Operations: The whole preparation is of no use if security components are not maintained. First, organization needs to create a policy set on determined data between data in motion, at rest, or in transit category. Split the entire DLP operation into three phases i.e., Triaging, reporting and escalation, and tuning phase.
- The triaging phase testing of the enabled data loss policy. The team of security operation will be monitoring alert alarm with help of DLP policies.
- The incident reporting and escalation phase involves assigning of incident to their respective team from security persons. For forensic investigation purpose, the archiving of the records plays a vital role in entire process.
- The tuning phase involves passing of each data with a false positive result. The team of security is responsible for refining the entire policies, which are setup in DLP software.
Final Verdict
Data loss prevention technique is a brilliant and preventive technology to keep confidential data safe in an organization. It is important to make good DLP strategy because then, actual one will be able to experience security from this security measure. Make sure that firm’s owner is investing money in right product, after properly understanding all the illustrated strategies.

