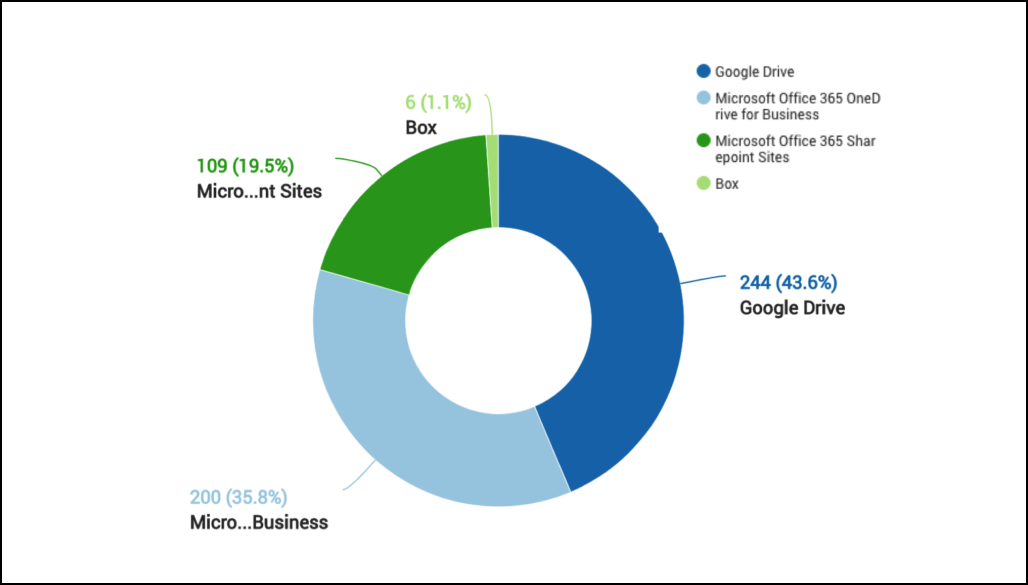
Financial Industries Have Lots of Insider Threats Risks – Let’s See How
Kumar Raj - December 26, 2018 ~ 5 Minutes Reading
In the financial industry, accountants and other officials are having role of managing, logging, and auditing the finance. They are properly trained in their respective education field regarding these common business activities. But, they are
Get Guidance on GDPR Compliant Privacy Policy Template For UK Firms
Kumar Raj - November 30, 2018 ~ 5 Minutes Reading
The EU general data protection regulation is a European union legislation whose purpose is to benefit EU citizens with tons of control over their information. According to this regulation, UK enterprises who deal with EU
Phishing Attacks in Retail Business Acts Like Bumper Sale for Attackers
Kumar Raj - November 16, 2018 ~ 5 Minutes Reading
The post is going to familiarize readers about the phishing attacks held worldwide when retail industries organize season sale. This time period is a big opportunity for hackers to attempt data breaches on targeted industry.
How Security of Chromebook Works – Let’s Figure Out
Kumar Raj - November 12, 2018 ~ 5 Minutes Reading
Google Chromebooks were coded with data security in mind. So, its time to see that how does the security of Chromebook works for the customers! One of the most common questions on social media regarding
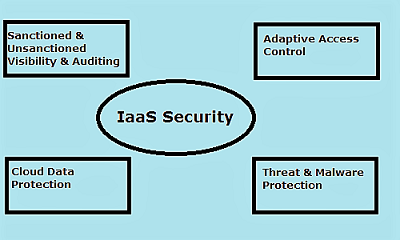
Get to Know About IaaS Security Risks In Cloud Computing
Kumar Raj - October 23, 2018 ~ 4 Minutes Reading
In today’s world of digitization, organizations are shifting their work to IaaS platform because of its flexibility and speed. Since it is a cloud-based concept, therefore, there exist IaaS security risks. It is so because
How to Import OLK14.contact to PST Format Easily
Nilesh - October 15, 2018 ~ 5 Minutes Reading
The OLK file extension is recognized by Outlook Address Book which contains the contact information of both people and organization. The OLK file format is developed by Microsoft to store names, contact numbers, addresses. titles,
Get Different Ideas on How to Add Custom G Suite Password Policy
Kumar Raj - October 12, 2018 ~ 5 Minutes Reading
Google Suite has become well-known than ever. With around three million paying enterprise clients, this cloud-based email app has become one of the most essential productive platforms in the world. But, a challenge occurs while
What is PII and Its Role Under General Data Protection Regulation?
Kumar Raj - October 3, 2018 ~ 5 Minutes Reading
Securing confidential information on cloud is a shared responsibility. Cloud service provider’s customers responsibility is to use associated services that comply with regulations, laws, and policies wherever needed. The European union GDPR commands enterprises to
CASB India – Get Guidance to Choose the Best From A Wide Marketplace
Kumar Raj - September 17, 2018 ~ 4 Minutes Reading
“Hello All! I am owning a big enterprise in Bangalore and using cloud computing technology for my official work for last 2 years. Earlier, I was able to handle the Cyberthreats on basic level by